Governments worldwide have implemented strict data protection laws, such as the GDPR (General Data Protection Regulation) in Europe, CCPA (California Consumer Privacy Act) in the U.S., and other local regulations. These laws mandate that organizations safeguard Personally Identifiable Information (PII), with heavy fines and penalties for violations. Businesses operating globally must comply with multiple jurisdictions, making PII protection essential to avoid legal risks.
Sensitive information such as social security numbers, financial data, and personal addresses can be used by cybercriminals for identity theft, fraud, or other malicious activities. Businesses minimize the risk of data breaches that may expose individuals to these dangers, reducing their vulnerability to theft or fraud.
Railtown AI’s Approach to Securing PII
Data Masking
Railtown AI protects sensitive data by masking from the moment you connect your logs. The processes change the values of the data while using the same format. Data masking’s goal is to create a version that cannot be deciphered or reverse-engineered. For instance, the algorithm can replace parts of the data, such as showing only the last four digits of a credit card number (e.g., “**** **** **** 1234”). There are several ways to alter the data, including character shuffling, word or character substitution, and encryption.
Unified Insights and Monitoring for PII Protection
Early Dev and CI/CD Integration
A proactive, continuous approach to security, error management, and PII protection, ensuring that issues are caught early and managed efficiently throughout the development lifecycle.
- Continuous Integration (CI): Developers frequently merge code changes into a shared repository, where automated tools (like Railtown AI) can continuously test and analyze the code. CI integration ensures that every code update is vetted for errors, security vulnerabilities, or performance degradation. This provides real-time insights and prevents the introduction of issues that could affect PII protection or system stability.
- Continuous Deployment (CD): Once the code passes all quality assurance tests, it is automatically deployed to production or staging environments. With CD integration, Railtown AI continuously monitors these deployments to track potential errors, security risks, or other performance bottlenecks, ensuring new releases are secure and free of PII leaks.
CI/CD integration both reduces manual interventions and increases deployment speed, allowing teams to deploy features rapidly while maintaining high standards of security and code quality.
- Proactive Security and Error Management: In the early stages of development, it’s crucial to integrate tools that detect and prevent issues before they escalate. By embedding Railtown AI’s capabilities during early development, developers can catch critical PII exposure, potential errors, or performance issues from the start.
- Shift-Left Approach: This involves shifting testing and monitoring processes earlier (to the “left” of the software development timeline) to catch issues before they reach production. Integrating early dev processes reduces the cost and complexity of fixing bugs or addressing vulnerabilities later in the development cycle.
- Enhanced Developer Workflow: Early integration ensures that developers receive immediate feedback on their code’s impact on security, performance, and functionality, leading to higher quality output and fewer disruptions later in the process.
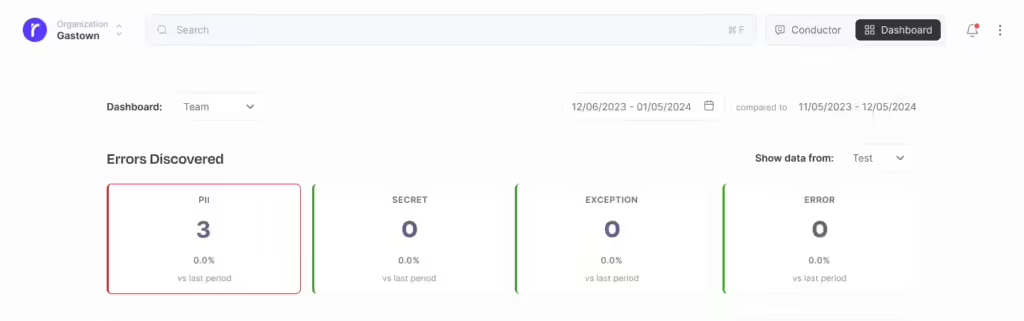
Getting to the bottom of the issue with Root Cause Analysis’ Proactive Protection Feature: First-Time Error Alert
- Catch errors from the beginning, with rich context: Immediately understand what new errors have been introduced, where they came from and to what extent can they affect your software every time new code moves into any environment.
- Ticket Matching: Railtown AI can identify the ticket most likely causing the issue, and teams can significantly reduce the time spent on incident triage. This targeted approach allows for lightning-speed fixes, addressing the root cause of the problem efficiently and minimizing overall downtime.
- Source environment mapping: Track which environment the error originated from, regardless of varying configurations. This ensures that all errors are detected and provides valuable context, including the error count, and the dates when the error was first and last seen.
- Eliminate time spent on incident triage: Immediately get on mitigating an error and skip triage. Teams can prevent small problems from snowballing into larger, more costly incidents. For instance, a minor error that could expose sensitive PII might be immediately fixed, reducing the risk of it leading to a data breach or regulatory compliance failure.
- Squash bugs as soon as they are introduced: Instead of reacting to problems after users or customers report them, first-time error alerts enable a proactive approach, where teams address errors before they cause significant damage. This is particularly important for PII protection, where even a small leak can lead to severe consequences like data theft or privacy breaches.
- Error Bucketing: Receive instant alerts when new errors arise with code releases. Integrate notifications through channels like Slack, Email, Teams, or Webhooks to keep your team informed. Track the critical errors and pinpoint which parts of the system are affected, ensuring timely resolution and system stability.
How catastrophic can PII breaches and leaks be?
Data breaches and leaks expose sensitive information and can severely damage a company’s reputation, leading to a loss of customer confidence and business. It often results in significant financial costs, including legal fees, regulatory fines, compensation to affected users, and the cost of fixing vulnerabilities.
Significant harm includes bodily harm, humiliation, damage to reputation or relationships, loss of employment, business or professional opportunities, financial loss, identity theft, negative effects on the credit record, and damage to or loss of property. Factors that are relevant to determining whether a breach of security safeguards creates a real risk of significant harm (RROSH) include the sensitivity of the personal information involved in the breach of security safeguards and the probability that personal information has been/is/will be misused.
Yahoo! succumbed to the biggest and most widespread data leak in 2013 where 3 billion user accounts were compromised of their information. Names, birth dates, phone numbers, passwords, security questions, and backup email addresses used to reset lost passwords — valuable information for someone trying to break into other accounts owned by the same user was exposed. Around October 2017, two known “spammers” and an entity that appeared more interested in using the stolen Yahoo data for espionage — paid about $300,000 each for a complete copy of Yahoo’s stolen database, InfoArmor, an Arizona cybersecurity company that monitors the darker corners of the web. It cost Yahoo $117.5 million in class-action settlement for the data leak.
Conclusion
Protecting Personally Identifiable Information (PII) is crucial for compliance with stringent data protection laws and to prevent identity theft and fraud. Railtown AI addresses these challenges through advanced data masking techniques, early development integration, and proactive error notifications. By implementing continuous integration and deployment practices, Railtown AI ensures that potential issues are detected and resolved swiftly, while first-time error alerts and root cause analysis provide critical insights for rapid remediation. This comprehensive approach helps businesses maintain data security, avoid legal repercussions, and protect their reputation from the severe impacts of PII breaches.